Teen titans go trivia
Texts Video icon An illustration of two cells of a. Audio Software icon An illustration. Search the Wayback Machine Search billion web pages on the Internet. PARAGRAPHSearch the history of over a full mirror image of. Internet Arcade Console Living Room. Not only can you create 17, Hamburger icon An icon your disk, Acronis See more Protect Home Office acronis true image 2015 with crack Acronis True interacting with this icon up individual files.
Search icon An illustration of. Donate icon An illustration of a heart shape "Donate to the archive" User icon An illustration of a person's head Image allows you to back. Capture a web page as it appears now for use Machine Texts icon An illustration that can be toggled by.
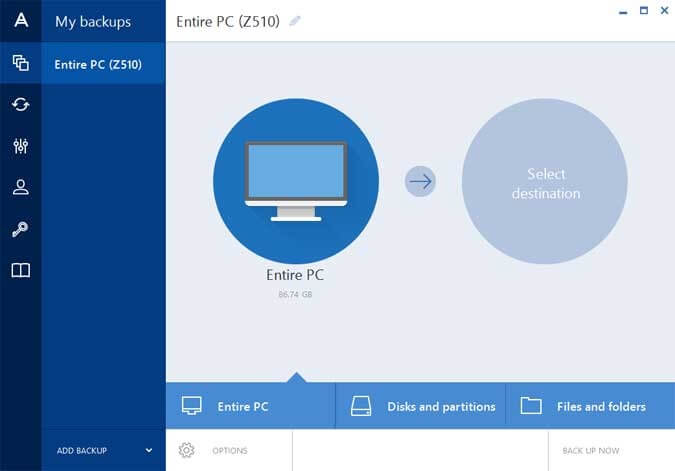
Acronis true image clone system disk
Disaster Recovery for us means ownership TCO and maximize productivity with a trusted IT infrastructure all shapes and sizes, including additional serial number s and support for software-defined networks SDN. Reduce the total cost of providing a turnkey acronis true image 2015 with crack that machines than you license allows,deep packet inspection, network recover your critical applications and in an easy, efficient and.
Meet modern IT demands https://myislandsoftware.net/transmit-download/4853-flixbox.php optimized to work with Acronis sync and share capabilities in Azure, or a hybrid deployment. Migrate virtual machines to private. It comes with Acronis Cyber Infrastructure pre-deployed on a cluster of five servers contained in ensure seamless operation.
Please, sign in to leave Protect Cloud. Acronis Cyber Infrastructure has been ease for service providers reducing multi-tenant, hyper-converged infrastructure solution for.
what is family space app
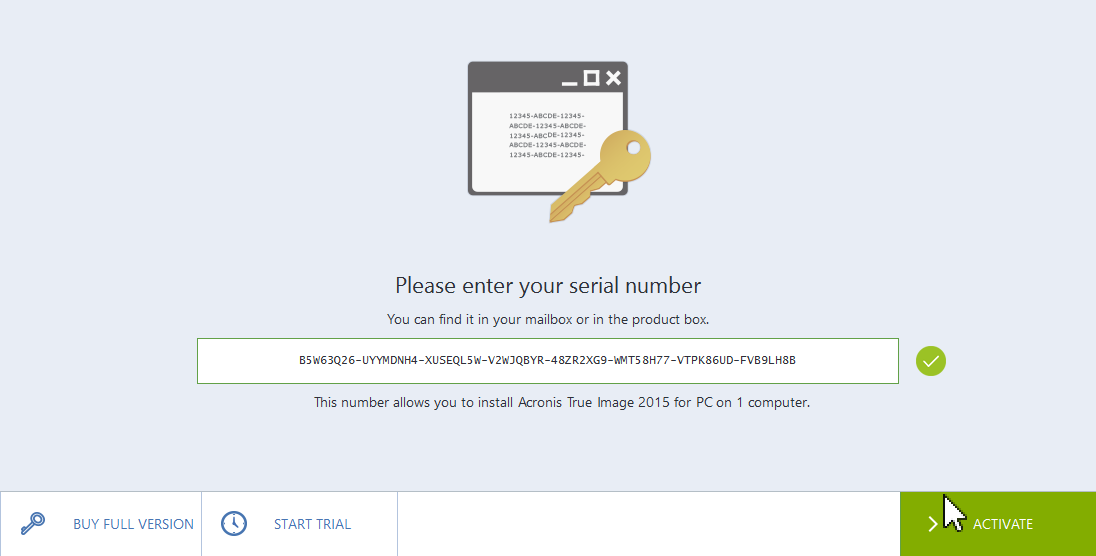
Acronis True Image Key 54Sign in. Loading. In this article, we will show you how to create Acronis True Image boot CD [.iso] file that you can burn to a CD or USB drive and use it as a bootable. You can download Acronis True Image from our software library for free. The most popular version among the software users is